During
week 5 of CYBR 650 there has been plenty of security news. The blog this week
will touch on a Microsoft zero day vulnerability and a data breach that
happened at the IRS. This Microsoft zero
day vulnerability is in Microsoft Office and allows remote code execution to
take place. This vulnerability affects all current versions of Microsoft
Office, which includes Office 2016. The vulnerability was first found by Ryan
Hanson in July of 2016. McAfee reported the zero day on Friday, but said
Microsoft has known about it since January (Goodin, 2017). Hackers are now
using this vulnerability to spread banking malware called Dridex. A word
document that has been specially crafted can be executed on a computer, which
allows an attacker to run code. The word document containing a malicious
OLE2link object is how the attack starts. This specific attack runs the exploit
code then makes a connection out to a remote server, where a malicious HTML
application file or HTA gets downloaded (Khandelwal, 2017). Once the HTA file
gets downloaded it runs and downloads different pieces of malware designed to
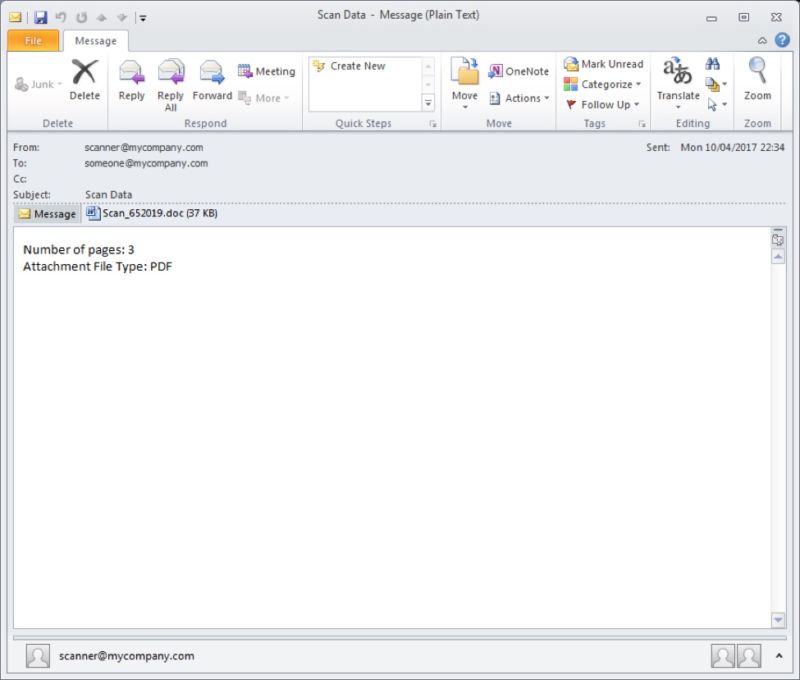
gain control of the computer or steal credentials. Below is a screenshot of a phishing email that
contains a malicious word document.
Microsoft has released a patch
yesterday to fix the vulnerability. This will stop the code from running if an
email of the word document gets through the security controls. The worst part
about this zero day is Microsoft has known about this and did not fix it. The
fix only came out after hackers were using it to spread malware via emailing a
word document. ProofPoint saw the new malware campaign and was able to block
the malicious word document.
The Internal Revenue Service or IRS has
had a data breach that may affect up to 100,000 people. The IRS has a tool for
FAFSA or Free Application Federal Student Aid that hackers have exploited. The
tool for FAFSA helped family and students complete the form because it is
lengthy. Since I’m I have gotten my associates, bachelors and currently getting
my masters I have had to fill out the FASFA forums. The FASFA forums are long
and are a pain to fill out. According to
Krebs on Security fraudsters may have been using the tool to get AGI or adjusted
gross income (Krebs, 2017). The IRS has disabled the tool because people were
starting to use it for fraud. The tool is called the IRS Data Retrieval Tool or
DRT. John Koshinen went before the Senate Finance Committee to testify that
less than 8,000 fraudulent returns were processed by the IRS (Cohn, 2017).
The good thing is the tool is
expected to be back online, but not till October. Does the IRS run any
penetration tests or security testing? It seems like their tools are put into
production without any testing and it is causing people to lose their personal
information. The IRS needs to provide protection to the users that were
affected from the breach. Companies that have had a data breach have provided
identity theft protection, but the government does not provide these
protections.
References
Goodin, D (2017,
April 11). Microsoft Word 0-day used to push dangerous Dridex malware on
millions. Retrieved April 13, 2017, from https://arstechnica.com/security/2017/04/microsoft-word-0day-used-to-push-dangerous-dridex-malware-on-millions/
Cohn, M. (2017, April
10). Data breach of IRS student financial aid tool may have affected 100,000
taxpayers. Retrieved April 13, 2017, from https://www.accountingtoday.com/news/data-breach-of-irs-student-financial-aid-tool-could-have-affected-100-000-taxpayers
Krebs, B. (2017,
March 21). Krebs on Security. Retrieved April 13, 2017, from https://krebsonsecurity.com/2017/03/student-aid-tool-held-key-for-tax-fraudsters/
Khandelwal, S. (2017,
April 11). Unpatched Microsoft Word Flaw is Being Used to Spread Dridex Banking
Trojan. Retrieved April 13, 2017, from http://thehackernews.com/2017/04/microsoft-word-dridex-trojan.html
No comments:
Post a Comment